Over the past few days we have seen an increased spread of a dangerous Ransomware virus…commonly known as Cryptolocker and Anti-viruses have been UNSUCCESSFUL in detecting it which is why we request your attention.
So what is a Crypto Locker virus ?
Crypto Locker is a virus which essentially encrypts (or in other words locks) all commonly known file formats such as doc, xls, jpg, pdf, mp3 etc. on your computer and whatever your computer is connected to with Military grade encryption mechanism making them unusable.
This means that if one of the employees in your business downloads this infection, the virus can potentially damage all files/folders that their PC is connected to including Network shares and files stored on the server making it inaccessible for everyone else… essentially bringing the business to a complete halt.
The virus makers then ask you to purchase the decryption key to unlock the files and the price you pay depends entirely on how many files they have managed to encrypt. From what we have read and seen ourselves, it could be anywhere from $600 – $9000.
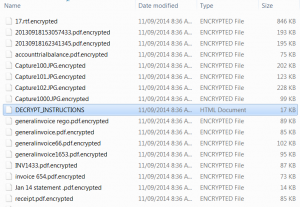
This is a view of how your files will look like once infection has penetrated.
And how do you get your files back if you did get infected?
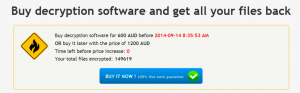
If your files did get infected there are literally only 2 ways out. One is to pay the ransom (as shown in picture below) via BITCOIN and hope that they do send you the decryption key
Second is to ensure that you have a good backup and Disaster Recovery(DR) strategy in place to recover your files from. In the case of one of our clients they could get their files back only because they had a good backup and DR system in place. Let’s say if you have a single backup disc with no disk rotation strategy in place, the disk connected to the PC/Server at the time will also be infected with the virus.
If you don’t have a good backup and DR strategy in place or are unsure if your backup system is regularly tested contact us on 1300 978 938 to discuss your needs.
A virus that outsmarts Antiviruses
Our clients that were infected with this virus last week had their Antivirus protection up to date and yet their entire network got infected. Luckliy for them they had a good backup system in place which was setup by MULINK due to which they only lost a few hours worth of work.
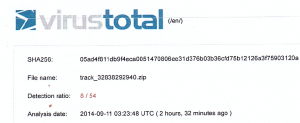
When we downloaded the infected file ourselves and ran a check against 54 popular Anti-viruses in the market today, only 8/54 (i.e. 15%) picked the file as being infected. Results as in picture below.
This Crypto locker virus is outsmarting the antiviruses because it uses patterns and signatures that antiviruses cannot detect unless the file is reported to them. In the case of our clients, we reported the file and the website the infection came from to 3 antivirus companies and within 12 hours of us reporting this, the detection ratio had gone up from 15% to 65%.
Where does the infection come from?
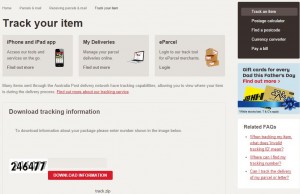
The most common ways we are seeing this virus spread is by Email Phishing i.e. the virus makers send you an email impersonating Paypal, Australia-Post or a Major Bank. You are then redirected to their website which looks exactly the same as these organisations (picture below). Innocent users are then coaxed into downloading a file, which when downloaded and run, starts penetrating through the files on your PC, network shares, USB devices etc. making them unusable.
What can I do to prevent infection?
Do not open any email that looks suspicious. If in doubt, check with your IT Consultants or organisations where they supposedly originated from.
Australia post and major banks have been warning people against opening such emails. Here is a warning issued by AUPOST last week – http://auspost.com.au/about-us/email-scam-warning-jul-2014.html
Secondly, refrain from downloading pirated movies/music/shows from bit torrents or other such p2p websites.
And lastly be aware…Spread the word by forwarding this to co-workers, friends and colleagues.
If you have any further questions/comments, post them below or contact our team on 1300 978 938